You can also take actions on files involved in an alert or incident. Figure 9.52 shows the actions available for files:
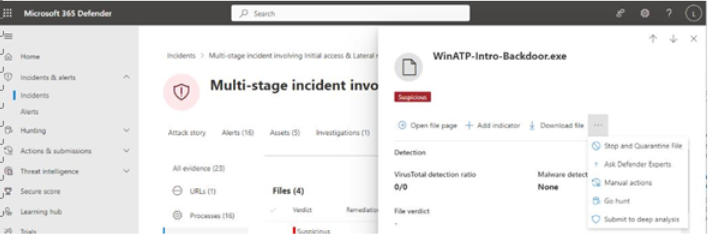
Figure 9.52 – File actions
The remediation actions listed in Figure 9.52 include the following:
- Download file: Package up the identified file and download it. This may expose your device to risk, so use it with caution.
- Stop and Quarantine File: Depending on the type of file, you may stop its execution, quarantine it to prevent it from being accessed, or both.
• Ask Defender Experts: An additional service available, Microsoft 365 Defender Experts allows you to ask Microsoft security personnel to help provide context around threats. For more information on Threat Experts, see https://learn.microsoft.com/en-us/ microsoft-365/security/defender/onboarding-defender-experts-for-hunting.
- Submit to deep analysis: Examine the file in a Microsoft 365 Defender sandbox. The analysis may take up to 3 hours.
Security analysts working with Microsoft 365 Defender have many options for investigating and remediating issues inside the platform.
Resolve
After you are done investigating an incident and resolving the problems, you can determine the disposition of the incidents and alerts.
To close out an incident, you can select the incident on the Incidents page and then click Manage incidents, as shown in Figure 9.53:
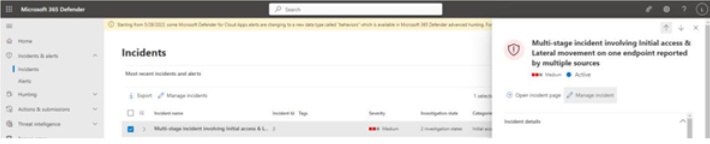
Figure 9.53 – Incident flyout
The Manage incident flyout appears, which allows you to update the incident name, add any incident tags, assign the incident to a security analyst, update the status, set a classification, and add any comments, as shown in Figure 9.54:
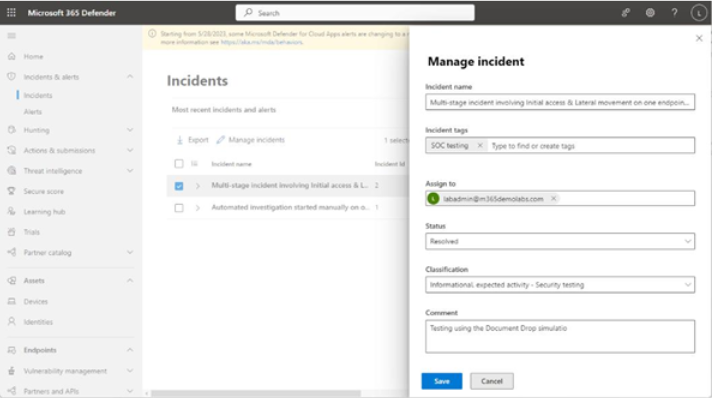
Figure 9.54 – Manage incident flyout
After updating the incident properties, you can click Save. Updating an incident’s status to Resolved automatically resolves all the active alerts associated with it. You can still view the story, alerts, and other associated information for further post-mortem analysis.
